UPDATED: May 8, 2025 16:15 ET
Remember the last time you felt bulletproof because your EDR was running? That sense of security can vanish in a heartbeat, especially when attackers use your own installer against you. A recent revelation shows how adversaries weaponize SentinelOne’s signed installers to knock its agent offline—and then drop Babuk ransomware without a hitch.
The Sneak‑In: “Bring Your Own Installer”
Think of it like a Trojan horse built with official markings: you launch the install, it shuts down all SentinelOne processes, and before the upgrade finishes, the bad guys pull the plug on msiexec.exe. Suddenly, your endpoint is stripped of its shield, and the attackers stroll right in.
That's exactly what the Stroz Friedberg Incident Response team discovered recently while investigating Babuk ransomware attack.
In this scheme, attackers deployed a legitimate, signed SentinelOne installer packages to trigger an agent upgrade. They then kill the Windows Installer process (msiexec.exe) mid‑update, leaving all SentinelOne services terminated and the endpoint unprotected.
With the EDR agent offline, the threat actors were able to install Babuk ransomware (a sophisticated, AES‑256‑based encryptor available as Ransomware‑as‑a‑Service) to lock files and demand payment.
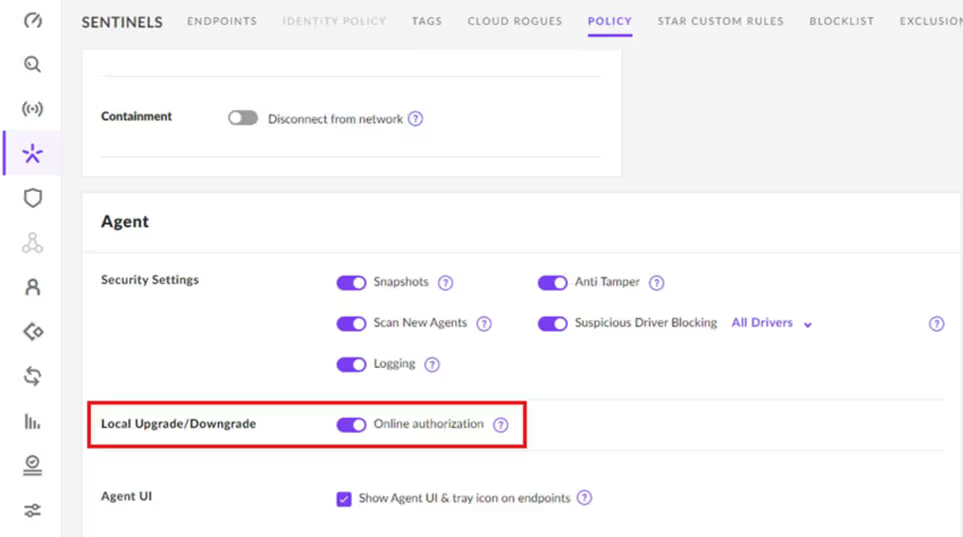
Lock It Down Before the Party’s Over
The fix isn’t rocket science, but it does require a quick policy tweak. To defend against this trick, SentinelOne advises enabling the “Online Authorization” policy, which blocks any local upgrade, downgrade, or uninstall without console approval, and recommends monitoring for unexpected version changes and abrupt service terminations in the Event Logs (EventIDs 1, 93, 1042).
Wrapping Up
The takeaway? Even the best endpoint defenses can be turned into a liability if left unconfigured. By treating your EDR like a living system—one that demands regular checks and policy reviews—you close the doors on stunt plays like “Bring Your Own Installer.” Because when your tools are locked down, the attackers lose their biggest advantage: stealth.
Update
SentinelOne has rolled out several new controls and detections to stop this BYOI bypass in its tracks:
- Local Upgrade Authorization GA (available since January 19, 2025): blocks all local agent upgrades by default.
- “Potential Bring Your Own Installer (BYOI Exploitation)” detection rule in Library → Detections: flags aborted MSI installs.
- Default enablement for new deployments: new accounts ship with Local Upgrade Authorization turned on.
- Agent anti‑tamper & passphrase enforcement: built into every agent, preventing unsigned uninstall/upgrade attempts.
Next steps:
- In the console go to Settings → Agent Management and confirm Local Upgrade Authorization is enabled.
- Under Library → Detections, enable Potential BYOI Exploitation.
- Optionally define maintenance windows for scheduled local upgrades.
For full details straight from SentinelOne, see their official announcement:
Protection Against Local Upgrade Technique Described in Aon Research



